Best scanops antivirus alternatives will be discussed in this article. Developers may integrate Scanops Antivirus, a completely customizable, cross-platform security scanning and virus analysis API, into their websites or programmes. It checks for viruses in JavaScript, HTML, and CSS, unlike conventional solutions. That implies that any website you create, regardless of whether you utilise a static site builder, may be secured against malware. The utility offers private or self-cloud hosting and is powered by many top-tier antivirus engines.
It works well for desktop or online applications when you wish to give your consumers real-time antivirus screening. You might, for instance, include Scanops into your programme so that users may scan any files they download or receive from other users to ensure their safety.
Top 15 Best Scanops Antivirus Alternatives in 2022
Top 15 Best Scanops Antivirus Alternatives in 2022 are explained here.
1. URLscan

This is another scanops antivirus. Prior to visiting any questionable URLs, rapidly scan them using URLscan.io for viruses, trojans, keyloggers, spyware, and other malware. Without putting any software on your computer, it retrieves the URL’s home page and runs a number of security tests. The tool will suggest whether or not it is safe to visit based on the findings. Also check BitGapps
This website examines the suspicious URLs from the perspectives of their look, behaviour, and content. The scanner will scan any URL you provide and display a list of all vulnerabilities. In some circumstances, it will also give you a link to an in-depth analysis of that vulnerability. Millions of malware signatures are compared by URLscan.io’s anti-malware engines against downloaded files.
2. Joe Sandbox

Joe Sandbox is a Deep Malware Analysis application powered by artificial intelligence (AI) that uses sandboxing techniques to discover malware and sophisticated threats that are not picked up by regular antivirus programmes. The solution offers unprecedented visibility into a company’s digital footprint as the distinctions between malevolent and lawful purpose become more and more hazy. Joe Sandbox provides a Sandbox API that permits programmatic access to all of its capabilities in addition to a graphical user interface that enables highly trained users to build unique automated studies.
These comprise special formulas and heuristics, in-depth research into the behaviour of malware, aggressive memory scanning, decompiler technology, malicious URL identification, and many other things. As a cross-platform tool, it may be used with Linux, Mac OS, Android, iOS, Windows 7, 8, and 10. In conclusion, Joe Sandbox is a fantastic tool that you may take into account as one of your options.
3. AbuseIPDB

Internet users can use the AbuseIPDB online database to see if the IP address they are using is blocked by any global security measures. The database of registered IPs, which may have been used for illegal activities like hacking, spamming, botnet management, etc., may be searched by users. The database includes information from several real-time blacklists and blacklist databases.
It is highly helpful for those who are going to create an email address or register for any online service and want to see if the address has previously been used. Additionally, you may report any other IP due to any fraudulent, spam, or harmful conduct. This will update the database and assist others in identifying.
4. MalShare

Access to malware examples that have been reported by users is made possible through MalShare, a public malware repository. By offering malware samples in an intuitive and accessible manner, it aims to assist security firms, virus researchers, and the general public. It offers users collaborative features for incident response and malware research, as well as the option to upload and download malware samples. This is another scanops antivirus.
With a search bar and recently conveyed samples, the interface is straightforward. Each file has the following information: source, file type, date and time of addition, SHA256 Hash, and Yara Hits. Overall, it’s a fantastic tool for locating hidden hazards, which are frequently dispersed via open file sharing networks.
5. VxStream Sandbox

Security experts can recognise and respond to cutting-edge threats thanks to Hybrid Analysis, a comprehensive malware analysis tool that was formerly known as VxStream Sandbox. On any Windows workstation, it offers a secure environment for the execution of malicious files without compromising the host system. You may execute malware in a controlled, isolated environment that won’t infect your host machine in order to better comprehend and identify it.
You may accomplish this without owning your own hardware by using VxStream Sandbox. You may easily launch any malicious file thanks to this. Review findings quickly and simply using a straightforward online interface, analyse suspicious files in a highly adaptable sandbox, and more.
6. Malwares.com

A database system is provided by Malwares.com, a web-based harmful code detection tool that enables users to gather and exchange the most recent dangerous codes in real-time. Additionally, gather, produce, evaluate, and disseminate information on dangerous programmes. This type of intelligence-sharing system can assist businesses in keeping track of the most recent harmful software on the market, acting before it spreads and mitigating the risk. Also check appsflyer
Based on sophisticated pattern matching algorithms and security monitoring technologies with a low false-positive rate, the system can do autonomous analysis. Users may acquire the most recent information about this type of threat, including its identity, path, consequences, and potential countermeasures, by using the knowledge of harmful codes gathered by the system. Users can always be aware of the state of harmful programmes thanks to the system’s sophisticated statistics on data collecting.
7. VMRay Analyzer Platform

The top enterprises in the world employ the VMRay Analyzer Platform, an internet security threat analysis and detection solution, to defend against advanced persistent threats, 0-day attacks, data breaches, network traffic monitoring, and endpoint activities. The scalable solution uses proprietary smart sandbox technology and machine learning to detect assaults that eluded traditional antivirus programmes. This brand-new cutting-edge technology is intended to provide businesses a thorough understanding of online risks and abnormalities in real time at speeds of up to hundreds of gigabits per second.
It combines sophisticated algorithms for security threat identification with adaptable and potent data mining capabilities, all backed by a top-notch visualisation engine. It helps security professionals to identify and assess security risks, identify and isolate impacted systems, and estimate the consequences of a breach in real time. From the ground up, VMRay Analyzer was created to be quick, light, and very versatile. This is accomplished by employing carefully designed data structures that enable the detection algorithms to operate quickly while consuming little memory.
8. Buster Sandbox Analyzer
This is another scanops antivirus. A process behaviour change analysis and malware activity tool called Buster Sandbox Analyzer enables you to keep an eye on a portfolio of programmes and send you notifications when it finds abnormalities or unwelcome behaviour. The tool deals with the expanding issue of targeted assaults on businesses. Any significant antivirus software can be used in conjunction with it to enhance its capabilities.
It may be utilised by malware analysts for malware reverse engineering and research as well as by cyber security teams for malware analysis. Windows executable files, documents, PDFs, Zip files, and self-extracting archive files may all be analysed by the Buster Sandbox Analyzer. It is simple to upload any suspicious file and submit it for additional examination thanks to the interaction with VirusTotal.
9. Triage
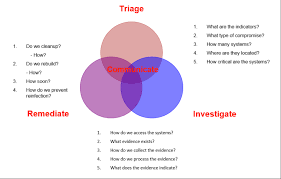
Triage is a simple-to-use and trustworthy cybersecurity analysis sandbox that enables anybody to look at the behaviour of malware. Its user-friendly interface enables analysts and developers to design experiments, enabling anybody to look at cloud-based malware without any technical expertise or prior Malware Analysis experience. You may utilise it on Windows, Android, macOS, and Linux thanks to the cross-platform compatibility. To check whether your concerns are true, it will intercept your file or network activity and execute it in a virtual setting.
Using Triage’s malware analysis sandbox, suspicious files and documents—from those that may contain malware to those that include embedded harmful macros—are examined. Malware can be downloaded via URLs or local files. It has a tonne of tips and methods for getting the most data out of a file and putting it back together again.
10. CyberGordon

An online reputation ecosystem called CyberGorod defends consumers, professionals, and businesses from internet crooks and their weak IP addresses and domains. It provides a special approach for rating and enhancing websites’ reputations based on user comments. Both big and small businesses use it to acquire research on possible sites to restrict them and stop a data breach. It gives consumers access to a thorough background in cyberspace as well as the person’s current behaviours, which are developed using data from forums, blogs, social networking sites, and public sources.
In order to find cyber risks, it scans and searches through more than 80 different types of data, including social media, business directories, online archives, deep/dark web, mobile applications, and more. Based on the total weight of all supplied information, the algorithm assigns each account a ranking. The procedure produces an actionable report that you may use to make more informed decisions about your accounts and prevent unintentional online infractions.
11. VirSCAN

To find and remove malware from shared files, use the multi-engine online virus scanning VirSCAN. The utility makes use of the capabilities of numerous anti-virus engines rather than just one, which may overlook some threats. As a result, your files are searched for dangers multiple times. Additionally, VirSCAN provides a variety of scanning options along with a file repair option that cleans damaged files and fixes virus code. It is quick and doesn’t require any installation. This is another scanops antivirus.
Simply upload your PC’s files or folders and check to see whether they are contaminated with viruses. You may scan files up to 20MB in size, and when the scan is finished, you will receive a report with any risks that were found. It also offers a description of any viruses discovered, which may be useful in deciding if the file is infected or not. This is a fantastic feature. Additionally, VirSCAN updates viral definitions immediately minutes after a new infection is found.
12. Quttera

With the help of the online malware scanner Quttera, you can scan your website and receive a thorough report on the security dangers it faces and the potential effects they may have on your company. The most crucial aspect of running a website is safeguarding the private information you store there. However, rather than being caused by sophisticated software flaws or server problems, the majority of cyberattacks originate from websites themselves. Websites are examined by Quttera to make sure that no malware, spyware, phishing, or other online frauds are present.
Its innovative technique is based on ongoing, extensive research of domain name reputation as well as real-time behaviour monitoring of files and websites. Additionally, it actively recognises sophisticated threats that have never been observed before without producing false positives. Only special, proprietary technology that examines and picks up on every threat you face can make this feasible.
13. MetaDefender

MetaDefender is a solution for advanced threat prevention and detection that employs machine learning to automatically detect and neutralise sophisticated cyber attacks. It blends intelligence and behavioural analytics with the quickness and ease of a cloud solution. This next-generation security system supports real-time intelligence from the Dark Web and has no false positives or tweaking. This cutting-edge technology enables enterprises to actively defend themselves against complex cyber-attacks by doing a forensic study on each threat. Also check 9Apps
This is another scanops antivirus. When an organisation uses MetaDefender, sophisticated cyberthreats may be swiftly identified, investigated, and stopped before it’s too late. It offers comprehensive visibility into activity on the network and across websites. The application can identify and stop ransomware, phishing assaults, malware, and other harmful web material thanks to the company’s exclusive Dynamic Behavior Analysis engine. Overall, MetaDefender is a fantastic alternative that you should take into account.
14. FAME Automates Malware Evaluation

For cyber security experts, FAME Automates Malware Evaluation is a method that automates the assessment and identification of suspected malware samples. It facilitates security firms’ analysis of the behaviour of dangerous programmes, which would otherwise be a painfully slow procedure. It will be possible to evaluate the characteristics of ransomware samples and test their resistance to the many existing defences using this simple-to-use application.
Making sure the analysis tools they use are precise enough to provide an accurate assessment of the malware sample is one of the most crucial tasks for any cyber security analyst or researcher. This is crucial when the code being examined has the potential to seriously harm a machine or network. Every time a new sample is submitted to the database, FAME changes the definitions and scans. Overall, it’s a fantastic open source virus scanner that you may take into account as one of your options.
15. Any. Run

Any. Run is an online malware sandbox and memory debugging tool that mimics real-world behaviour by employing methods that malware in the wild use. When testing with actual malware, it enables researchers to quickly examine the behaviour of harmful code and prevents them from crashing their own virtual computer. To build a predictable and reproducible environment for research purposes, the tool does all the grunt work. This is another scanops antivirus.
This programme includes a variety of activities that may be utilised immediately in a malware analysis environment, including modules, anti-debugging hacks, anti-VM tactics, and more. It is not simply restricted to reverse engineering. These procedures can be used to analyse malicious executables both dynamically and statically. The tool may be included into any current analytical workflow and provides a strong API. Since there is no need for installation, it is incredibly convenient to deploy and use on all machines.

